With the upcoming 5.2 version, Matukio will support Boulderado cash software. Boulderado is an (german) all in one cashier software solution for the Windows PC. It offers an intuitive interface, making it easy to sell tickets and more at your (local) sites! The integration automatically syncs all events and bookings to Boulderado and vice versa. Making it easy to sell (or just book) events over your website with Matukio and also at your local site! When a new booking is created in the cash software, it is automatically submited to Matukio. Support includes booking confirmation emails, notifications of the organizer by Matukio and more! You can also do a cash payment at the site and Matukio automatically enables the booking and can generate and send the invoice!
A bit earlier then planned Matukio 5 is now available for download! Bringing tons of changes and new features to our Joomla events extension. If you are in a hurry and just want to take a look at the new responsive bootstrap 3 frontend visit our demo page!
New responsive frontend
Matukio 5 brings a completely rewritten and improved frontend based on the bootstrap 3 framework. The new design is 100 % responsive and looks great on every device, from smartphones, over tables to large desktops. The frontend is now also completely jQuery based and does no longer need Mootools. And we did not only rewrite the public views, but also the frontend organizer area, so you have a continuous look & feel throughout the whole extension. But it is not only a design update, there are also a lot of new features in the different views!
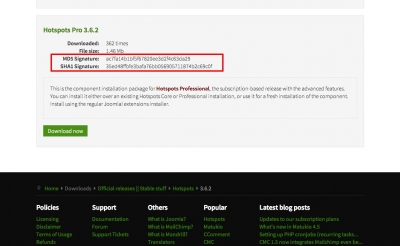
Recently I was doing some research on sites offering our paid Joomla Pro extensions for "free" download. I took the first result of a simple Google search (Extension name + Download) and came to a huge Joomla and wordpress focused extension warez site (There were hundreds of paid Joomla extensions and templates for "free" download). The website did not look like the typical warez site, it looked pretty reliable, did not have dubious advertisements and they also provided a short description, extension voting and a direct link to the file (which downloaded without any pay-gates or any other typical warez troubles). There was also a virus total scan link which reportedly belonged to the downloadable file too.After downloading the first thing I noticed was that the filename was different to our normal naming scheme. So the next step was checking the md5 / sha sum of the file, you can do this on Linux / Unix directly with the terminal - on windows there are a lot of (GUI) programs for that too. These hash sums make files clearly recognizable, protecting you from man in the middle attacks or manipulated download packages. That's the reason we show them for every file on our download pages - you should always check if the sum matches the package ones.
The result was that the hash sums did not match - So somebody definitely changed something in the package. Funny fact is that the hash sum also didn't match to the provided virus total scan - so the scan was also a fake. So I run another virus total scan in expectation to get a very different result (e.g. trojans in it), but the result was none (!) of the 54 antivirus programs detected anything.So I unpacked the package and started with searching for changed files - I knew the packaging date of the original files was almost 350 days ago, so I looked for changed files since then. You can't completly rely on the modified date, because it is easy to manipulate it, but in this case they seemed to be too lazy for changing it back. So the result was that 4 files had been changed and 2 new were added, on February, 20th 2014 - almost 6 month after the release.In the list of the changed files was the main entry script for the extension installation, the script.php file and the hotspots.php in the administrator backend. The new added files were allegedly harmless images, both called social.png in two different folders. But let's take a look at the changes in the script.php first - they just added a single line at the end of the file:<?php include('images/social.png');?>There it is, a PHP include for the new "image" file. Funny fact is that they also closed the normal PHP tag before, so they don't seem to have much experience with PHP, but that does not make it less dangerous. The administrator hotspots.php file had just the same include at the end - let's take a look at this mysterious file (I formated it a bit).So if you installed that package - gratulations your website has been hacked and is probably now serving as a spam / malware host! The fake image file is a pretty large (52 KB!) obfuscated webshell PHP script. Funny fact is that it does not only support Joomla! installations but also wordpress based websites. What does the script do? Because the script is pretty large and it would require a lot of work to decode it complelty I just walk you through some obvious noticable things. First thing the script does is registering a new (plugin) handler to onAfterRender to your Joomla! system, which creates a new table called options (Yes the script also provides an easy settings storage for the owner of the script!) and installs itself into the system. Next it seems to collect some informations about your website and your host and sends that (via email) to an encoded address, with the subject "Phone Home".The script owner can now upload and change files, update / create database entries and do almost everything with your installation. The script even encrypts the communication with the control server with a nice openssl connection (They use the PHP function openssl_seal with a included ssh public key for that).